Computer & Network Security
Category : Banking
Computer & Network Security
Computer security (also known as cyber security or IT security) is information security as applied to computing devices such as computers and smart phones, as well as computer networks such as private and public networks, including the whole Internet.
Traditionally, computer facilities have been physically protected for three reasons:
For example, military and civilian institutions in the government often restrict access to information to those who need that information. The first formal work in computer security was motivated by the military's attempt to implement controls to enforce a "need to know" principle. This principle also applies to industrial firms, which keep their proprietary designs secure lest their competitors try to steal the designs. As a further example, all types of institutions keep personnel records secret.
TOP SOME SOURCES OF COMPUTER VIRUS ATTACK
The most potent and vulnerable threat of computer users is virus attacks. Virus attacks hampers important work involved with data and documents. It is imperative for every computer user to be aware about the software and programs that can help to protect the personal computers from attacks. One must take every possible measure in order to keep the computer systems free from virus attacks. The top sources of virus attacks are highlighted below:
TYPES OF ATTACK IN NETWORK SECURITY
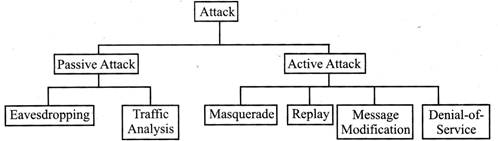
In Network Security, attack is typically divided into two parts.
Passive attack further divides into two parts:-
Active attack further divides into four parts:
In a message modification attack, an intruder alters packet header addresses to direct a message to a different destination or modify that data on a target machine.
TOP ATTACKS IN NETWORK SECURITY
There are some important network security Attacks are:
MALWARE
Malware, also known as malicious software, is a software that is used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It can appear in the form of executable code, scripts, active content, and other software. 'Malware' is a general term used to refer to a variety of forms of hostile or intrusive software. The term badware is sometimes used, and applied to both true (malicious) malware and unintentionally harmful software. Some malwares are:
A computer virus or worm is program that replicates itself on its own by by inserting copies of itself into other programs or documents. It can spread by email also. These viruses or worms are malicious programs that are designed to infect and gain control over a computer without the owner's knowledge.
Virus-makers and spammers create viruses that infect most of the computers across the globe. These computers become spam-generating machines and cooperate in various manners to send as much spam as possible as efficiently as possible. The infected computers then send massive amounts of spam, unbeknownst to the computer owner.
TYEPS OF VIRUS
There are various types of computer viruses, classified in terms of techniques, origin, the types of files affected, damage, OS or Platform attacked, as well as the places they hide. Some of the common types include the following:
ACTION OF A VIRUS
Different computer viruses create different problems in different ways. The most common problems are:
COMPUTER WORMS
A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program.
TROJAN
Trojans are malicious programs that perform actions that have not been authorized by the user. These actions can include:
Disrupting the performance of computers or computer networks Unlike computer viruses and worms, Trojans are not able to self-replicate.
SPYWARE
Spyware is software that aids in gathering information about a person or organization without their knowledge and that may send such information to another entity without the consumer's consent, or that asserts control over a computer without the consumer's knowledge.
SOME IMPORTANT TERMS RELATED TO SECURITY
Spoofing: It is a situation in which a program successfully masquerades as another by falsifying data and thereby gaining an illegitimate advantage. IP address spoofing or IP spoofing is the creation of Internet protocol (IP) packets with a source IP address, with the purpose of concealing the identity of the sender or impersonating another computing system.
Hacking: Hacking is the practice of modifying the features of a system, in order to accomplish a goal outside of the creator’s original purpose. The person who is consistently engaging in hacking activities, and has accepted hacking as a lifestyle and philosophy of their choice, is called a hacker. Computer hacking is the most popular from of hacking nowadays, especially in the field of computer security. But hacking exits in many other forms, such as phone hacking, etc. and it’s not limited to either of them.
Cracking: The original difference between cracking and hacking is that hacking were those who attacked/penetrated security systems of networks while crackers were those that attacked/penetrated security systems of software. Crackers, cracked software (not networks system) such that they could be pirated. Crackers are the profit side of the coin. Their motivation is financial gain and/or cause damage. Crackers tend to be working for organized crime, services for hire, US, Chinese, Russian government employees, competitors commiting corporate espionage etc.
Phishing: It is the attempt to acquire sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication.
Spam: Spam is most often considered to be electronic junk mail or junk newsgroup postings. Some people define spam even more generally as any unsolicited email. However, if a long-lost brother finds your email address and sends you a message, this could hardly be called spam, even though it is unsolicited
Adware: Adware is the common name used to describe software that is given to the user with advertisements embedded in the application. Adware is considered a legitimate alternative offered to consumers who do not wish to pay for software. There are many ad-supported programs, games or utilities that are distributed as adware (or freeware). Today we have a growing number of software developers who offer their goods as “sponsored” freeware (adware) until you pay to register. If you’re using legitimate adware, when you stop running the software, the ads should disappear, and you always have the option of disabling the ads by purchasing a registration key.
Rootkits: A rootkit is a type of malicious software that is activated each time your system boots up. Rootkits are difficult to detect because they are activated before your system’s Operating System has completely booted up. A rootkit often allows the installation of hidden files, Processes, hidden user accounts, and more in the system OS. Rootkits are able to intercept data from terminals, connections, and the keyboard.
SOLUTIONS TO COMPUTER SECURITY THREATS
Some safeguards or solutions to protect a computer system from accidental access are described below:
Ensure that reputable anti-virus software is installed on all computers. This should include all servers, PCs and laptops. If employees use computers at home for business use or to remotely access the network, these PCs should also have anti-virus software installed. Everyday new computer viruses are being released and it is essential that businesses are protected from these viruses by keeping the anti-virus software up to date. If possible, companies should look at policies whereby computers that do not have the most up to date anti-virus software installed are not allowed to connect to the network.
As computer viruses can spread by means other than email, it is important that unwanted traffic is blocked from entering the network by using a firewall. For users that use computers for business away from the protection of the company's network, such as home PCs or laptops, a personal firewall should be installed to ensure the computer is protected.
Firewall
A method for keeping a network secure. It can be implemented in a single router that filters out unwanted packets, or it may use a combination of technologies in routers and hosts. Firewalls are widely used to give user access to the Internet in a secure fashion as well as to separate a company’s public Web server from its internal network. They are also used to keep internal network segments secure. For example, a research or accounting subnet might be vulnerable to provide firewall protection.
All incoming and outgoing email should be filtered for computer viruses. This filter should ideally be at the perimeter of the network to prevent computer viruses. E-mails with certain file attachments commonly used by computer viruses to spread themselves, such as .EXE, .COM and .SCR files, should also be prevented from entering the network.
Ensure that all files downloaded from the Internet are scanned for computer viruses before being used. Ideally this scanning should be done from one central point on the network to ensure that all files are properly scanned.
Most computer viruses and worms try to exploit bugs and vulnerabilities within the operating system and applications that companies use. New vulnerabilities are introduced into networks every day, be that from installing new software and services, making changes to existing systems or simply from previously undiscovered vulnerabilities coming to light. It is important to regularly review your network and the applications running on it for new vulnerabilities. Any discovered vulnerabilities should be rated and prioritised regarding their criticality and the potential business impact they could have. Once this has been done, a plan on how to manage those vulnerabilities, either by patching, upgrading, or managing the vulnerability using tools such as firewalls or Intrusion Detection Systems should be put into place.
The creation and publication of an Information Security Policy is key to ensuring that information security receives the profile it requires in the organisation and is the first critical step in securing the company's systems and data. It is important that senior management support the Information Security Policy and that all users are made aware of their roles and responsibilities under this policy.
A password is an unspaced sequence of characters used to determine that a computer user requesting access to a computer system is really that particular user.
Strong password: Term used to describe a password that is an effective password that would be difficult. to break. Often a strong password has between six and ten characters (the more the better), numbers, other characters, and both upper and lowercase characters. Below is an example of a strong password.
Weak password: A password that is not an effective password because it's easy to remember. Names, birth dates, phone numbers, and easily guessable words are considered weak passwords. Below is an example of a weak password.
Many websites use certificates or digital certificates to define their security and identity, so that computers visiting the sites know the sites are legitimate and feature proper security. These certificates must be obtained and from the proper organizations, as well as registered with them. They also expire and must be renewed to remain valid. A web browser may deny access to a website or at least warn the user when a website's certificate has expired and the identity or security of the site cannot be verified.
Alternatively referred to as digitally signed, a digital signature is a mathematical scheme used to verify the authenticity of a digital document or message. They are used when determining authenticity and avoiding tampering are important, such as in financial transactions.
Digital signatures are often used as a means to implement electronic signatures that are encrypted which allows for both authentication and non-repudiation (the signer cannot deny signing a document while claiming his/her private key has not been compromised).
FILE AND FOLDER PERMISSIONS
Most current file systems have methods of assigning permission or access rights to specific users and group of users.
|
Permission |
Meaning for Folders |
Meaning for Files |
|
Read |
Permits viewing and listing of files and subfolders |
Permits viewing or accessing of the file's contents |
|
Write |
Permits adding of files and subfolders |
Permits writing to a file |
|
Read & Execute |
Permits viewing and listing of files and subfolders as well as executing of files; inherited by files and folders |
Permits viewing and accessing of the file's contents as well as executing of the file |
|
Modify |
Permits reading and writing of files and subfolders; allows deletion of the folder |
Permits reading and writing of the file; allows deletion of the file |
|
Full Control |
Permits reading, writing, changing, and deleting of files and subfolders |
Permits reading, writing, changing and deleting of the file |
SECURE SOKET LAYER
The Secure Sockets Layer (SSL) is a computer networking protocol that manages server authentication, client authentication and encrypted communication between server and client.
TRANSPORT LAYER SWCURITY
Transport Layer Security (TLS) is a protocol that ensures privacy between communicating applications and their users on the Internet.
IP SECURITY PROTOCOL
IPsec (Internet Protocol Security) is a framework for a set of protocols for security at the network or packet processing layer of network communication.
IP-sec is said to be especially useful for implementing virtual private networks and for remote user accessthrough dial-up connection to private networks.
IP-security protocol provides two choices of security service:
(i) Authentication Header (AH), which essentially allows authentication of the sender of data.
(ii) Encapsulating Security Payload (ESP), which supports both authentication of the sender and encryption of data as well. Earlier security approaches have inserted security at the Application layer of the communications model.
A big advantage of IP-sec is that security arrangements can be handled without requiring changes to individual user computers. Cisco has been a leader in proposing IP-sec as a standard (or combination of standards and technologies) and has included support for it in its network routers.
You need to login to perform this action.
You will be redirected in
3 sec
